If you get the following issue when you login, this is typically due to the fact that you do not allow users to use 3rd party application.
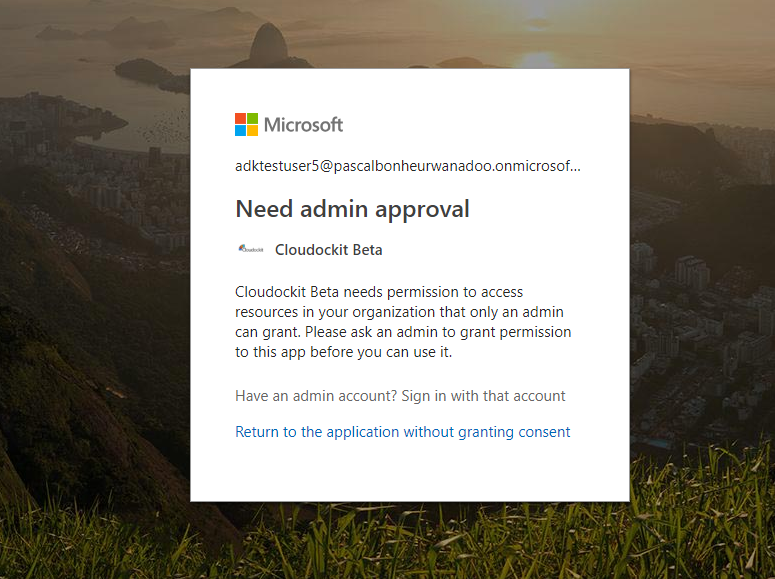
You can confirm that by checking the Users/Users Settings option in the Active Directory:
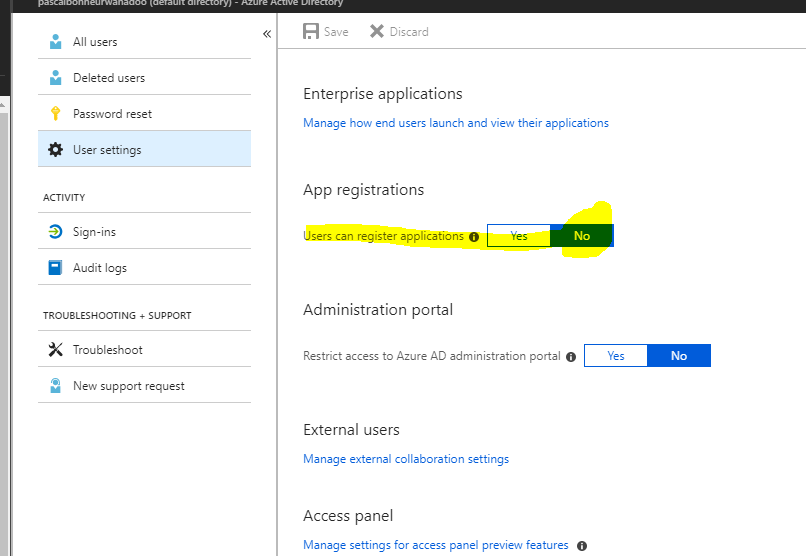
In order to fix that, you need to give admin consent to Cloudockit so that users without Global Admin permissions can use it.
You need to follow this procedure:
Important note: The procedure needs to be done with a global admin account.
• Navigate to portal.azure.com and login with a global admin account
• Select the default Azure Active Directory tenant of the subscription that you want to document (will be called mytenant.onmicrosoft.com for the rest of the procedure)
• Navigate to the Enterprise Applications selection, select All Application and type Cloudockit.
• You will see two Cloudockit applications :
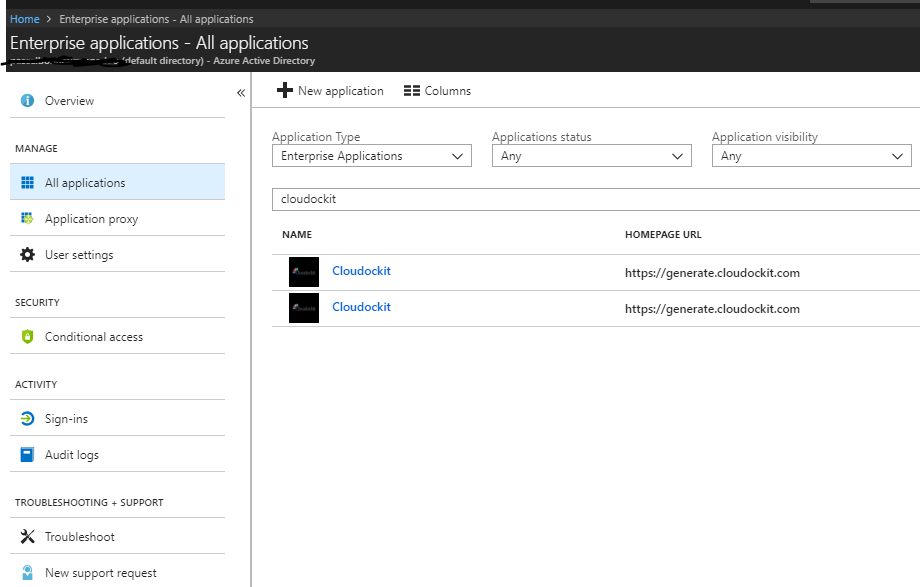
• Delete the two Cloudockit applications (this is required as we want that the consent framework pop again).
a. Note that there are two applications as there is one to login to Cloudockit first and then one to login to your Azure subscription with management rights
• Logout from portal.azure.com
• Navigate to https://generate.cloudockit.com
• Login with the global admin
• You will be prompt as follow :
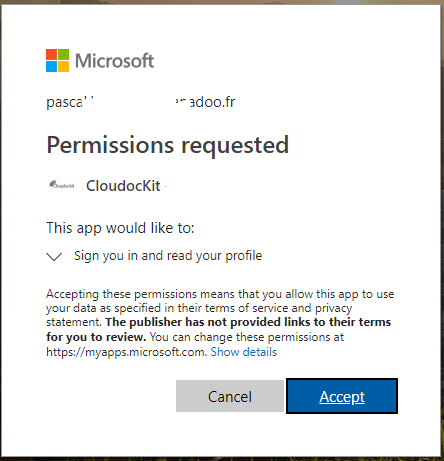
• Notice that the URL looks like this :
https://login.microsoftonline.com/mytenant.onmicrosoft.com/oauth2/authorize?api-version=1.0&response_type=code&client_id=8fcdfc51-26…
Replace all the begining of the URL before client_id with
https://login.microsoftonline.com/mytenant.onmicrosoft.com/adminconsent?
So that the URL looks like this
https://login.microsoftonline.com/mytenant.onmicrosoft.com/adminconsent?client_id=……com/LogIntoCDKWithAAD/CatchCode
Hit enter and you will be redirected to another consent question (which is actually admin consent). Click accept.
As there is currently no landing page for admin consent (we are working on it), you will see the following page :
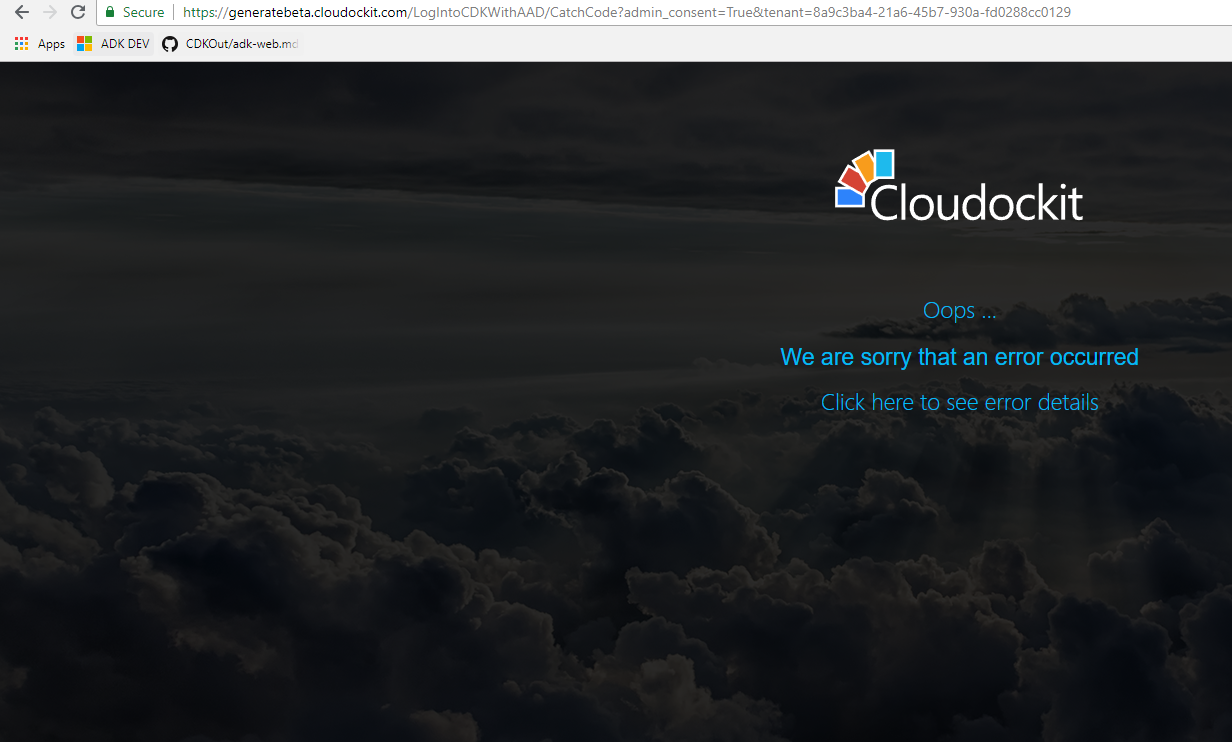
• Navigate back to https://generate.cloudockit.com and login again.
• Notice that nothing prompt
• Now, click on Microsoft Azure and we will do the same steps for the second Active Directory Application :
- Replace the URL from
https://login.microsoftonline.com/mytenant.onmicrosoft.com/oauth2/authorize?api-version=1.0&response_type=code&client_id=01f6d860-d06c-4586-9fa6-439ed7ba3365&resourcehttps://management.core.windows.net/&redirect_uri=https://generatebeta.cloudockit.com/LogIntoAzure/CatchCodeAzure&state=eyJUZW5hbnRJRCI6InBhc2NhbGJvbmhldXJ3YW5hZG9vLmdddddddd
to
https://login.microsoftonline.com/mytenant.onmicrosoft.com/adminconsent?client_id=01f6d860-d06c-4586-9fa6-439ed7ba3365&resourcehttps://management.core.windows.net/&redirect_uri=https://generatebeta.cloudockit.com/LogIntoAzure/CatchCodeAzure&state=eyJUZW5hbnRJRCI6InBhc2NhbGJvbmhldXJ3YW5hZG9vLmdddddddd
Click Accept.
You can now logout from portal.azure.com,close the browser and navigate with a non global admin account and you will be able to login.
This procedure will be supported without this URL modifications in a near future.